“In this blog we will understand what is multi-tenancy and how we can create scalable architecture for such type of Multi-tenant architecture for a SaaS Application”
How does multi-tenancy work, and why is it used by businesses? NET 7 multi-tenant database design for SaaS applications.
What is multi-tenancy?
One instance of a software application can serve multiple clients under a multi-tenant architecture. We are known services use multi-tenant architecture like Amazon, flip cart and others. One database is shared by the users of this service. Multi-tenancy is the term used here.
Single-Tenant VS Multi-Tenant Architecture
Single-Tenant Architecture: An application serving only one client is referred to as a single-tenant architecture. Tenants receive their own instance of an application and each user must configure its own instance, ensuring complete data isolation. Scalability and flexibility are also limited. It also limits scalability and flexibility.
It is Multi-Tenant Architecture: where one instance can serve multiple clients with the same features, they are isolated from one another for safety reasons, and each customer can only see their own data. This model is known for cost effectiveness.
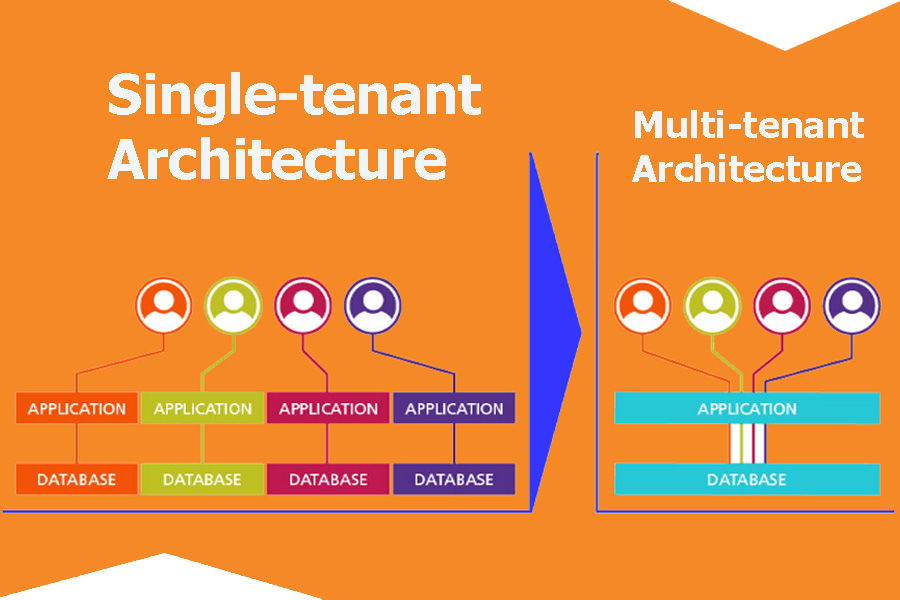
The first part of this example shows the typical single-tenant application, which requires separate deployments for each tenant. The term “tenant” describes the user community or the Organisation / Company that wants to use our programme. As you can see, each tenant will require a complete deployment of the infrastructure.
In contrast, a single deployment of an application is shared by several tenants in the second example. The tenants can decide whether to share the database.
Table of Comparison: Benefits and Drawbacks of Single-Tenant vs. Multi-Tenant Cloud Architecture
| Characteristic | Single-Tenant Architecture | Multi-Tenant Architecture |
| Economy of cost | Higher expenses because each tenant receives specialized resources | Tenant collaboration in sharing resources effectively can save total costs |
| Personalization | High degree of control and personalization | Accommodates shareable feature improvements and customization |
| Reliability | Restricted scalability due to resources allocated specifically for each tenant | Facilitates the smooth expansion of infrastructure and resources in response to tenant growth |
| Privacy and data security | Provides every renter with total data isolation and control | Strong data isolation procedures are necessary to guarantee data security and privacy |
| Updating and maintaining | Upgrading and maintaining each tenant separately is necessary | All tenants may receive updates and maintenance at the same time |
| Efficiency and steadiness | Investing in dedicated resources can boost stability and performance | Infrastructure and shared resources may have an effect on stability and performance |
In most situations, multi-tenancy is the better option, even though each architectural paradigm has pros and cons. Proper implementation enables the creation of a future-proof and scalable platform that maximizes resource utilization and is less difficult to maintain over time.
Multi-tenant Database Access
Shared database: Data is separated among tenants in these strategies, but tenants share the same database. Data access credentials are unique to each tenant. It is a simple and cost-effective method. Its database structure will look like this.
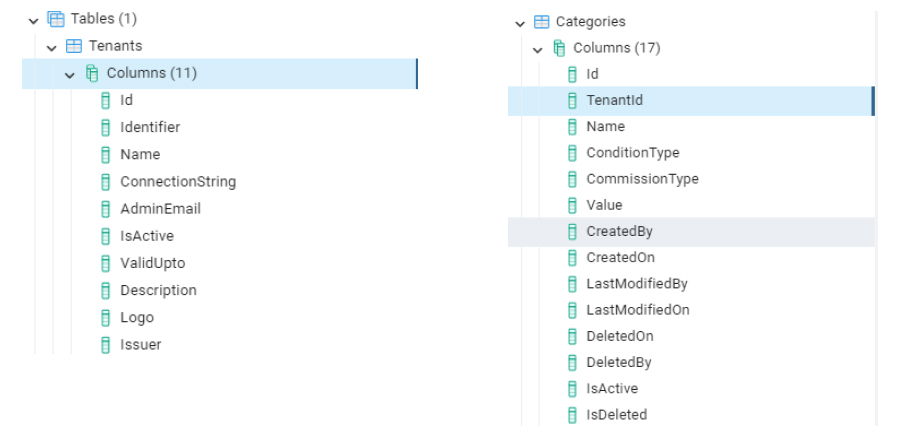
Challenges Associated With Multi-Tenant Architectures
Tenants sharing the same resources is a major cause of problems in multi-tenant design. This section will describe these difficulties and how you can overcome them.
The best security practises must be used in a multi-tenant architecture to increase security
Authentication and Authorization: To ensure that only authorised users have access to sensitive data, use robust authentication and authorisation mechanisms.
CORS: Bypassing a Web browser’s Same-Origin policy is possible with Cross-Origin Resource Sharing. A server app adds extra HTTP headers to inform browsers that it is okay to load pages (from its origin) in a small number of chosen client apps (of various origins). We can overcome with below solution.
Identifying Tenants by Strategy
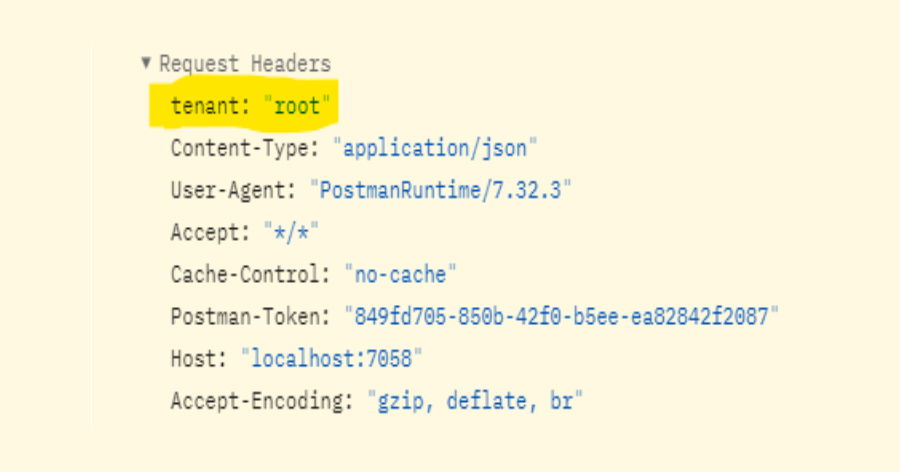
Request Header: This method of tenant identification is more effective. There will be a TenantID Header in each request. Once the request has been fulfilled for that specific tenant, the application closes. When requesting Authentication Tokens only, this method is advised to be utilised. In our tutorial, we will apply this methodology.
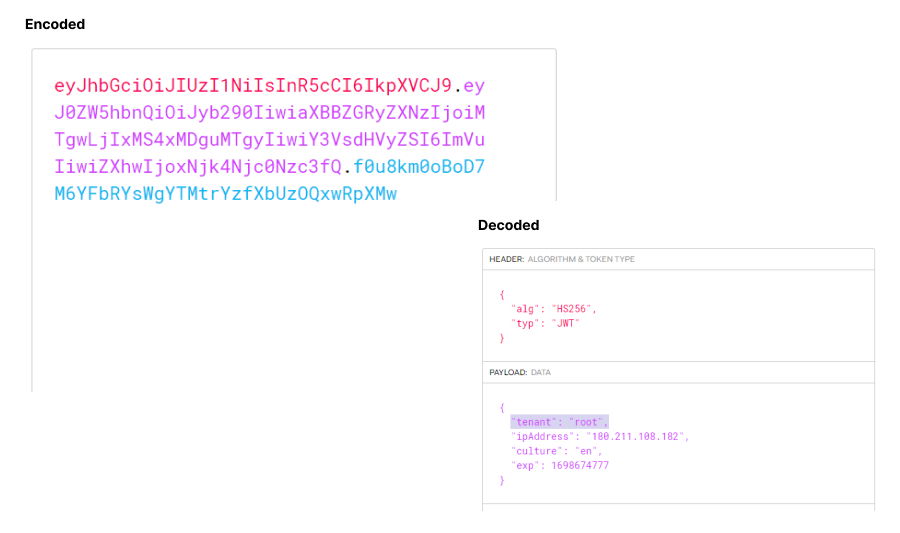
Query string: In the Server Variables collection, the QUERY_STRING variable is parsed into the Query String collection. The QUERY_STRING variable can be retrieved by name using this method. When we use parameters with Request. Query String like ? TenantId=root’
Claims:
How a Multi-Tenant SaaS Should Be Designed
Building efficient multi-tenant SaaS apps with an emphasis on resource sharing, customization, and scalability is what our company does best. The methodical approach we use to create a productive multi-tenant SaaS application is provided here.
- Creating the necessary conditions for tenant isolation in step 1: The process begins with determining the appropriate degree of separation between tenants for the application logic, data storage, and user interface layers. To create a secure and scalable system that can be customized to meet the needs of different tenants, it is essential to understand the level of isolation.
- Making a database strategy decision in step 2: The type of application and amount of data it contains determine which strategy type is best. Smaller businesses might initially benefit from shared databases, but as their user base grows, they might need to switch to a hybrid approach that allows them to scale resources across user groups.
- Using tenant identification in step 3: A tenant ID is one of the mechanisms we design to help identify tenants across the system. Data isolation and tenant-specific customizations should be preserved by using this identifier consistently in the application logic, user interface, and data storage layers.
- Creating scalable application components in step 4: Scalability is taken into consideration while developing the modules or microservices that make up your application. As a result, the application can effectively distribute resources among tenants, even as the number of tenants increases, and maintain consistent performance.
- Setting up settings particular to a tenant in Step 5: By developing a configuration module or service that keeps and controls each tenant’s settings, we offer tenant-specific customizations. Tenants can now have customized experiences without interfering with other tenants thanks to this.
- Protecting information and managing access in Step 6: To safeguard tenant data and manage resource access, we put strong security measures in place. To protect privacy of data and adherence to legal requirements, it has tenant-specific authentication, authorization, and encryption systems.
- Organizing for oversight and control in Step 7: We include tools for management and monitoring when we design your multi-tenant application. All tenants will experience a consistent and dependable service thanks to the effective detection and resolution of performance or security issues made possible by this.
- Making the best use of resources in Step 8: We use strategies like auto-scaling, load balancing, and caching to effectively manage resources like CPU, memory, and storage. This method maintains application performance while optimizing resource usage and lowering costs.
- Verifying and testing in Step 9: Before deployment, we thoroughly test your multi-tenant application under a variety of scenarios, including concurrent access, tenant-specific customizations, and resource contention, to find and fix any potential problems.
These procedures help us create a multi-tenant SaaS application that is secure, scalable, and adaptable to the various needs of our tenants while maximizing resource usage and financial effectiveness
Conclusion:
It takes careful planning and consideration of numerous technological factors to construct a reliable multi-tenant architecture for a SaaS application. You may efficiently serve numerous tenants while ensuring your SaaS application’s scalability, security, and performance by putting the recommended practises mentioned in this blog into practise.
A successful and profitable SaaS business is built on a solid multi-tenant architecture, therefore keep that in mind.
All product and company names are trademarks™, registered® or copyright© trademarks of their respective holders. Use of them does not imply any affiliation with or endorsement by them.




 Insurance
Insurance